Security &
Private Networks
Fortinet and Managed Firewalls
Network Security Planning
Professional Services
Network Architecture
As Network Hacking Strategies Get Ever More Sophisticated, Network Security has Become a Constantly Moving Target.
In order to protect your data as much as possible, it’s essential that you stay on top of the latest trends for network attacks and the newest prevention technologies. Your business depends on it.
Firewalls
A typical Firewall is a security device that sits at the edge of your business IT network. Working as the gate keeper to your internal network, a Firewalls job is to authorise what kind of data can be received and also, regulate what type of data it will allow to leave. Alongside keeping your incoming and outgoing data safe, a Firewall will also deny unauthorised entry from suspicious external sources that may attempt to remotely access your internal network to pray on your data by creating security breaches and cyber attacks. These types of attacks can pass viruses through your network which in turn, infect your IT infrastructure.
As you will have heard medical professionals say – “prevention is better than cure”. This is exactly the primary function of a basic Firewall; to prevent the issue in the first instance. At the edge of your network, and before getting close to business sensitive information. As such, a firewall should only be one aspect of a company’s IT security protocols deployed to protect your business.
A typical standard firewall only takes care of part of your network, in which case, there are many additional security protocols that businesses should use in other parts of their network to keep their data and their users safe and sound. They include;
- Malware Protection – This is software or hardware that stops the impacts of malicious software intentionally designed to cause damage to computers and servers on your network, including computer viruses, worms, Trojan horses, ransomware, spyware
- Anti-virus (AV) – This can be used as end user software or central hardware in order to detect and destroy computer viruses that have entered your network
- Anti-spam – These are services and solutions that focus on blocking and mitigating the effects of illegal email. (Spam)
- DDOS Protection – This can be a cloud- based protection service that protects against Denial of Service. This software analyses and filters illegitimate requests to pass secure information, usually to websites.
- Policy Protection – Sometimes found on ‘Next Generation Firewalls’, policies enable you to give access to the parts of a business network or external websites that you want people to have access to. Policies enable you to safeguard your people as well as your network.
- Secure VPN’s – Normally set up between a compatible network Firewall and an end users laptop or PC, VPN access creates a secure tunnel to enable your staff always-on access to your central servers, safely.
- Multi- Factor Authentication – Many businesses use FA is used as a security access sanity check. This can be accessible in many forms including a fob that creates a passcode, to an app generated through a smartphone.
As one starts to delve deeper, it becomes more that as there are multiple pieces of hardware and software needed to keep a network protected. Things can start to look rather convoluted, as if just one of those factors were to fail, a business could quite quickly see a domino effect on the rest of their network.
This is where ‘Next Generation Firewalls’ come in to their own, providing a more unified solution in addressing the primary network security needs of businesses.
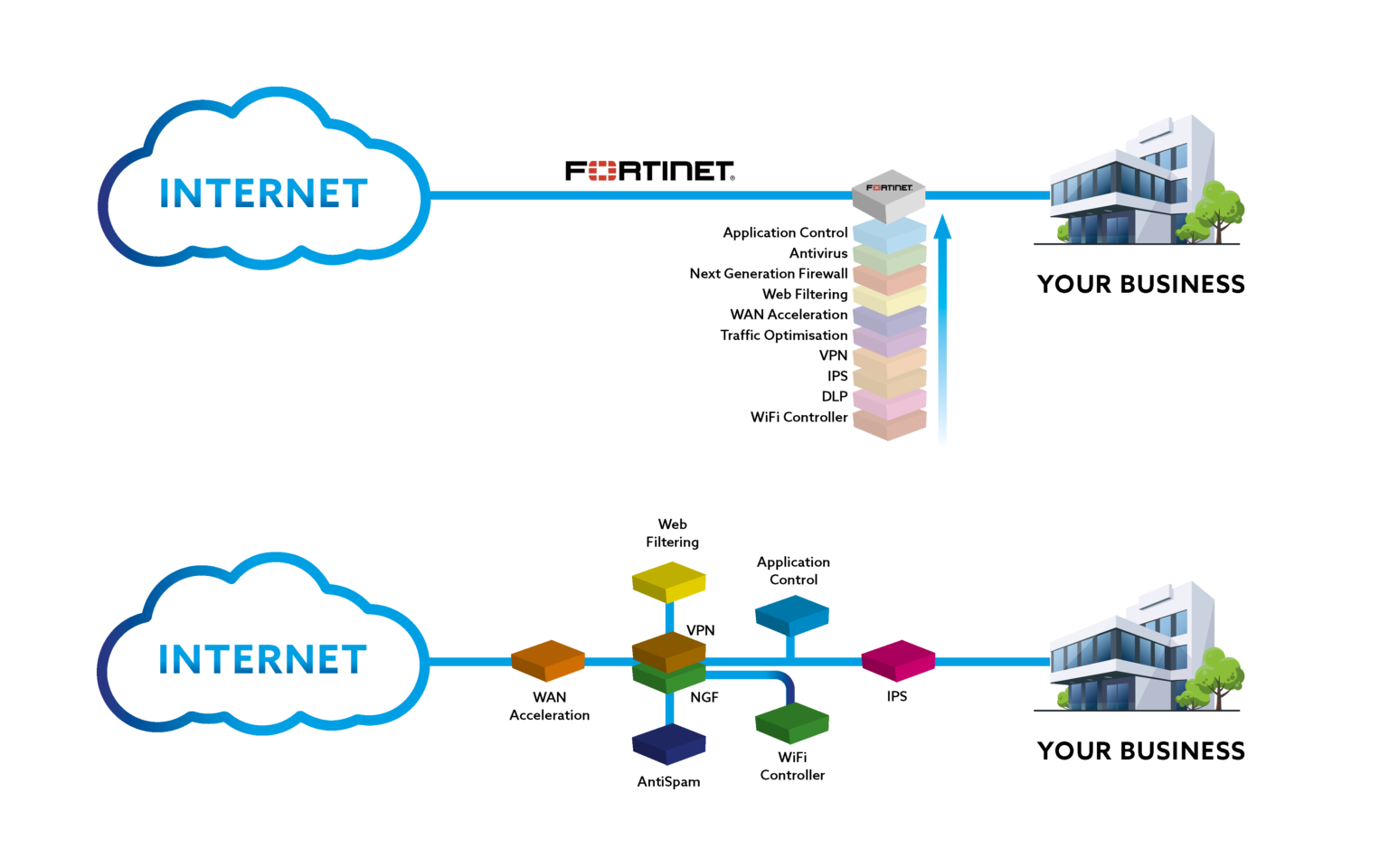
Next Generation Firewalls are network security devices that have constantly evolving internal software. Understanding that Cyber threats are a moving target, as hacking attacks are constantly morphing and mutating, a Next Generation Firewall is constantly downloading new information to the device in real-time. This enables them to handle the latest threats as soon as they have been identified.
Due to the sophistication and constant evolution of the software within Next Generation Firewalls such as Fortigate, they are sold as a licensed device. Normally with a 1 or 3 year operational duration. As Next Generation devices are licensed, it enables them access to real-time benefits like software updates that change their internal definitions of viruses and malware. This enables them to spot and protect against the latest viruses and malware before they can even get close to entering your network.
Operating system updates to implement security patches as will be required from time to time –is a much more involved job and generally requires a trained expert to migrate the system configuration across to the device itself once the updated firmware is in place. So, if you are not in the business of doing this day to day it’s best to have the support of a company that can assist in managing this for your business. With the FortiSupport contract IC offer we can do all this for you; and if additional work needs doing or your require the work to be done during anti-social hours, with our support package we will do this as well as anti-social hours working for you at half our standard hourly rate.
What Can a Next Generation Firewall Do for My Business?
Next Generation Firewalls are very sophisticated computer based systems, to get the best from them, they require complex configuration by specially trained engineers. When correctly configured, they deliver benefits to your business such as:
- Secure VPN’s – They allow Virtual Private Network (VPN) access from offsite workers to securely log into your internal network using a private tunnel without leaving a gap for hackers to gain access to your company network.
- Secure Integration to Cloud Based Systems – They allow safe integration with cloud based servers such as Amazon Web Services (AWS) and Microsoft ‘AZURE’ to name but a couple. This allows the businesses to have secure outsourced IT infrastructure and backup capabilities minimising company administration of IT.
- Flexible Networks – They allow seamless secure multi-site working with a shared network; whether you have one site and a couple of salesmen on the road that need to log in to your network to provide quotations to customers OR have 30 offices and 300 remote users – they allow businesses to have a secure network without ‘leaving the door open’.
- Active Directory – They can be linked to the organisation’s end user Microsoft logins so that access to internal network features can be linked to access groups. This helps to control access to features and permissions whilst minimising the room for ‘human error’ mistakes. This can include remotely limiting VPN access and the services available when connected, access to specific machines, networks or applications.
- Policy Protection – They allow the control of all applications across the organisation rather than the traditional basic filtering of network ports. As above, this application based filtering can be linked with Microsoft Active Directory for user based control.
- Malware Protection – This is software or hardware that stops the impacts of malicious software intentionally designed to cause damage to computers and servers on your network, including computer viruses, worms, Trojan horses, ransomware, spyware
- Anti-virus (AV) – This can be used as end user software or central hardware in order to detect and destroy computer viruses that have entered your network
- DDOS Protection – This can be a cloud- based protection service that protects against Denial of Service. This software analyses and filters illegitimate requests to pass secure information, usually to websites.
- Policy Protection – Sometimes found on ‘Next Generation Firewalls’ such as Fortigate, enables you to give access to the parts of a business network or external websites that you want people to have access to. Policies enable you to safeguard your people as well as your network.
- Secure VPN’s – Normally set up between a compatible network Firewall and an end users laptop or PC, VPN access creates a secure tunnel to enable your staff always-on access to your central servers, safely.
- Multi- Factor Authentication – Many businesses use FA is used as a security access sanity check. This can be accessible in many forms including a fob that creates a passcode, to an app generated through a smartphone.
Securing all data communication both in to and out of your organisation, (including web browsing and Voice over IP phone systems), Next Generation Firewall Services combine traditional firewall features with other network device filtering functions. By using in-line deep packet inspection (DPI) of the data as it passes through the firewall, the next gen device can provide an intrusion prevention system (IPS) as well as anti-virus scanning, checking for attacks and also monitoring all data leaving the network to check for and prevent data leaks. Where other Next Generation Firewalls can have their limitations, this comprehensive functionality and feature rich components make Forigate a high class device of choice.
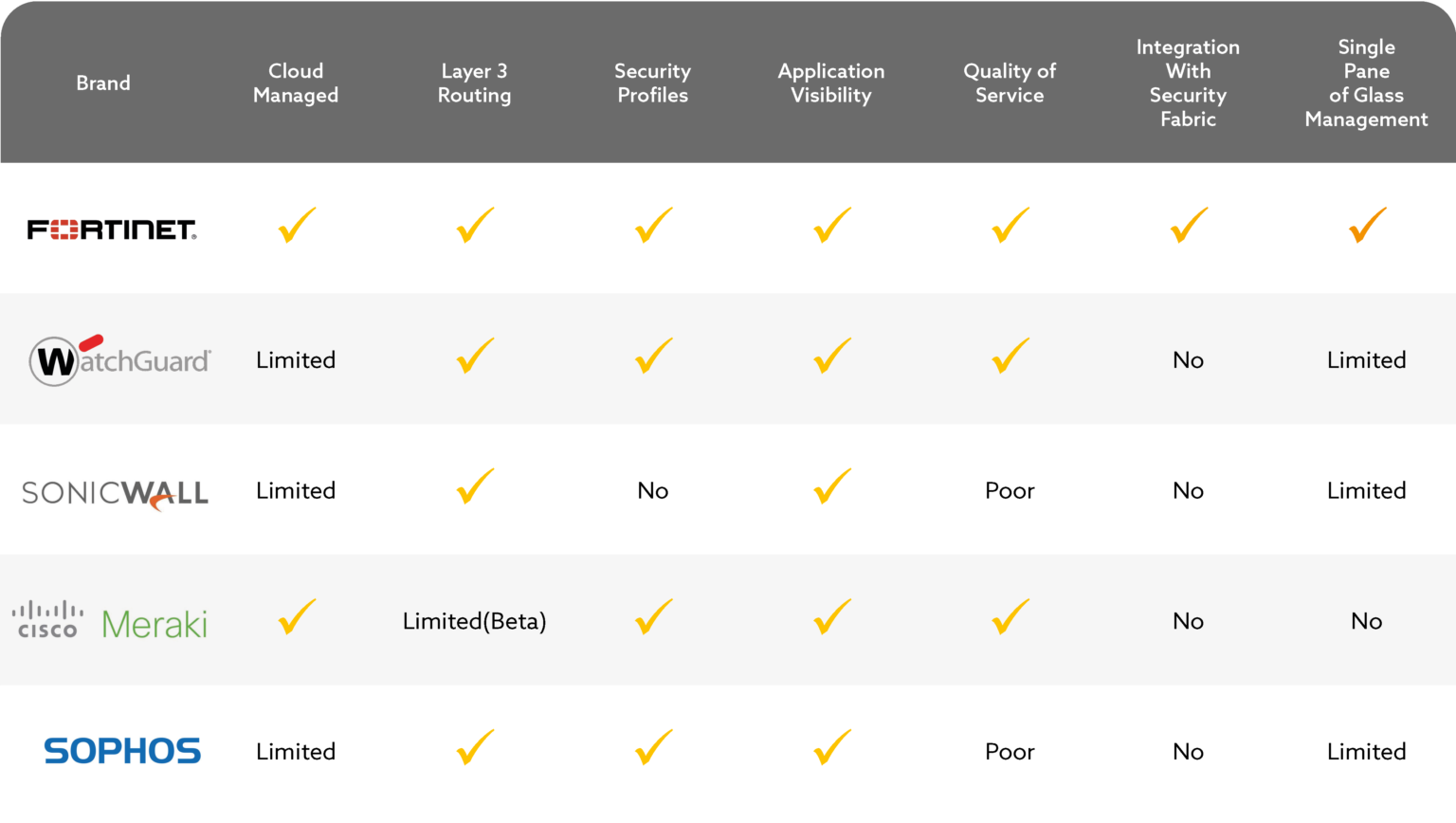
Due to the complexities of processing high volumes of data at high speeds, a Next Generation Firewall can often be a restriction on the high speed internet connection your business needs, (usually without you realising) so picking the right one for your business is crucial.
Choosing the correct device, perfect for the way your business will use it most efficiently isn’t as straight forward as it first appears as many manufacturers quote the ‘throughput’ of a Firewall with little or no threat protection enabled. (This is akin to purchasing the newest smart TV but not being able to watch any of the channels!)
Next Gen Firewalls advertised with a ‘throughput’ of 1Gb per second may (with all the protection and features we have outlined enabled) may achieve less than 1/10th of that speed because a device like a Fortigate will inspect each tiny packet of data that enters and exits your network. So when we talk about ‘throughput’, we are talking about fully analysed traffic. There are a number of features that can be independently switched on which are compute intensive. These include virus scanning, data leak protection, and inspection of secure encrypted web traffic.
Putting it into Perspective
If your business is using a 1Gb/s dedicated Internet connection, we generally find that they can opt to purchase a smaller Next Generation Fortigate device with a 700Mb/s throughput as this satisfies most operational requirements but at a more affordable price.
However, for data hungry businesses and larger organisations, (or those that perform external system backups), we would always recommend a higher specification of Fortigate. A larger device will enable a full 1Gb/s of throughput even with all additional Next Generation features invoked, and keep your Internet connectivity ready for your usual day-to-day operation, like ensuring your backups are completed overnight so as not to slow down daily tasks during working hours.
Do You Employ Additional Security Practices?
IC Recommends;
Regularly Back Up All Data (ideally to another location)
Whilst it’s important to prevent cyber attacks on your business, it is still possible to be breached regardless of your precautions. Therefore the backing up of word documents, electronic spreadsheets, databases, financial files, human resources files, and accounting files is a sensible way to ensure that even in the event of a breach, you could still retrieve your business data.
Be sure to back up cloud stored data to a location that you know you can find if you need it! To be doubly sure, companies store backups in a separate location in case of fire or flood in their main office premises.
Finally, when going to the effort of following rigorous back-up procedures, you should always check and do a test by retrieving your backups to make sure everything is functioning correctly and all your data is retrievable on a regularly scheduled basis.
Install Anti-virus/malware Software on Your End User Computers
It’s easy to assume that your employees know to never open phishing emails. However, employees are not infallible, especially as email scams are getting increasingly more elaborate. Since phishing attacks involve automatically and remotely installing malware on the end users computer when a link may be clicked, it is therefore essential to use anti-malware software installed on all devices on the network. These ‘insider’ phishing attacks can bypass the protection of any Firewall regardless of generation. IC both use and recommend FortiClient for end user protection as this can be used for anti-virus/malware protection as well as remote VPN access.
Use Multifactor Identification
Regardless of your preparation, employees are likely to make a security breaches that can compromise your company data by complete accident. Using the multi-factor authentication settings on most major network and email products is simple to do and provides an extra layer of protection.
Lock Down the USB Ports to Prevent the Use of Storage Devices
Preventing the use of USB storage may sound like an extravagant pain, but it removes a human approved route past the firewall for lurking and unfriendly software. It has the added benefit of helping to protect your data from loss or theft. In these cases, there will usually be a nominated ‘trusted user’ with USB storage access for an individual machine.
Implement a Plan for Mobile Devices
With the increasing popularity of Bring Your Own Device (BYOD) to work to help makes businesses more environmentally friendly,(be it mobile phones or wearables, such as smart watches and fitness trackers with wireless capability), it is essential to include and outline these devices in your security policy. ‘Norton’ by Symantec also recommends that businesses require employees to set up automatic security updates and that the company’s password policy apply to all mobile devices accessing the network.
Enforce Safe Password Practices
Yes, employees find changing passwords a pain. However, the Verizon 2016 Data Breach Investigations Report found that 63 percent of data breaches happened due to lost, stolen or weak passwords. At https://password.kaspersky.com/ you can do a simple check of your password strength to see how long it would take to break by a brute force attack.
In today’s BYOD world, it’s essential that all employee devices accessing the company network be password protected.
Educate all Employees
Next Generation Fortigate Firewall’s are one of the best protections of Cyber Crime and it will defend attacks from round the world by the minute. It will secure the doors and windows, that would be otherwise left wide open, of your internal infrastructure however it is vital your employees are educated in understanding how to spot scams. One of the best educations you can give is – “If you aren’t 100% confident you know what it is, don’t click it”. And just like the updates that a Fortigate receives, employees need to be refreshed frequently on your policies to ensure their security skill-set it kept up to date.
CASE STUDIES OF BUSINESSES WE SERVE...
- All
- Small
- Medium
- Large
Internet Central Limited
Innovation Centre 2, Keele Science Park, Keele, Staffordshire ST5 5NH
Registered Office: Ivy House Foundry, Hanley, Stoke-on-Trent ST1 3NR. Reg No. 03079542. VAT No. GB 278 923 705.
All trademarks and logos appearing on the site are the property of their respective owners. All prices exclude VAT E.&O.E.
© 2021 Internet Central Ltd.
01782 667700
sales@ic.co.uk











